Before the automotive cybersecurity standard ISO 21434 was introduced, the approach to cybersecurity was quite muddled.
The absence of standardized cybersecurity practices led to a fragmented landscape where each entity approached cybersecurity in its own way, leading to inconsistencies and vulnerabilities.
OEMs (Original Equipment Manufacturers) and Tier-1 suppliers faced a multitude of challenges that not only threatened the security and integrity of vehicle systems but also posed significant risks to safety and privacy.
So, what exactly did a standard like ISO 21434 change for the automotive cybersecurity landscape? For one, it introduced certain practices and methodologies that had a direct impact on making automotive solutions secure-by-design.
One such methodology is Threat Analysis and Risk Assessment, aka TARA. In this article, we will not only learn about the theoretical aspects of TARA but also understand how TARA is implemented, through a real-world example.
To get into the finer details of TARA, we brought in our cybersecurity expert, Ganapathi Ramachandra, Director of Engineering at Embitel Technologies.
Time to roll!
Threat Analysis and Risk Assessment in Action!
Since we are witnessing rapid innovation in ADAS, let’s put it under the lenses of TARA.
Let’s consider the challenge of cybersecurity within ADAS.
Advanced Driver-Assistance Systems (ADAS) enhance vehicle safety and driving comfort by automating operations, which could include steering, braking, and various other functions. However, these systems, due to their reliance on software, sensors, and connectivity, introduce various vulnerabilities.
Taking an example of Adaptive Cruise Control, hackers can exploit vulnerabilities in the communication protocol between the vehicle and the cloud or between vehicles (V2V) to send false information, causing the vehicle to brake unexpectedly or fail to adjust speed appropriately.
TARA steps in as the first line of defense, highlighting potential cybersecurity vulnerabilities and guiding manufacturers towards implementing robust security measures like encryption and real-time intrusion detection systems.
This proactive stance ensures that vehicles are not just technologically advanced but fortified against digital threats, safeguarding the integrity of ADAS and the safety of those who rely on them.
How to Perform Threat Analysis and Risk Assessment as per ISO 21434?
The execution of Threat Analysis and Risk Assessment (TARA) in cybersecurity engineering involves a detailed and systematic process to identify potential cybersecurity threats and assess the associated risks.
Although the standard ISO 21434 does not provide any strict method for performing TARA, it lays an outline for it.
The execution of TARA is a comprehensive process that involves multiple steps from pre-analysis to the definition of cybersecurity requirements, guided by structured approaches and methodologies. This ensures a thorough understanding of potential cybersecurity risks and the formulation of effective strategies to address them, thereby enhancing the security and resilience of automotive systems against cyber threats.
- Pre-Analysis Steps:
- Cybersecurity Item Definition: Begin by clearly defining the system under consideration, detailing its purpose, components, and boundaries. This sets the stage for a focused analysis.
- Critical Function Block Analysis: Analyze the system’s primary functions to pinpoint areas that are critical for operation and might be attractive targets for cyber threats.
- Technology Stack Analysis: Examine the hardware and software layers involved in the system. This includes identifying the technologies used and how they contribute to cybersecurity mechanisms.
- Threat Modeling: Develop conceptual models that represent potential cyber threats to the system. This step is foundational for identifying how and where a system could be attacked.
- Asset Identification:
Asset identification is a critical early phase in the Threat Analysis and Risk Assessment (TARA) process. It lays the groundwork for a comprehensive understanding of what needs protection within a system from potential cybersecurity threats.
This step involves systematically cataloging all components of a system that could be valuable targets for cyber-attacks or that are essential for the system’s operation and security.
Key Components of Asset Identification
- Hardware Components:This includes all physical devices and hardware within the system, such as servers, network devices, end-user devices, and any other equipment critical to the system’s operation.
- Software Elements: This encompasses the operating systems, applications, databases, and any other software that runs on the hardware components. Software elements are crucial for the functionality of the system and often contain or process sensitive information.
- Data: One of the most critical assets, data includes all information processed, stored, or transmitted by the system. This can range from confidential business information to personal data of users, which could be attractive targets for cyber attacks.
- Network Connections: These are the pathways that allow communication between components within the system and with external entities. These include both physical connections, like Ethernet cables, and wireless connections, such as Wi-Fi and Bluetooth.
- User Interfaces: This includes any point where a user interacts with the system, including web interfaces, command-line interfaces, and APIs. These interfaces can be pathways for unauthorized access if not properly secured.
- Cryptographic Keys and Certificates: These are used to secure communications and data and are themselves valuable assets that need protection against compromise.
Process of Asset Identification
- Inventory Creation: Compile a detailed inventory of all system assets. This should be as comprehensive as possible to ensure no component is overlooked.
- Asset Categorization: Group assets into categories based on their type, function, or sensitivity. This helps in prioritizing assets for risk assessment.
- Value Assessment: Evaluate the importance of each asset to the system’s overall operation and security. Assets critical to system functionality or containing sensitive information are of higher value and, thus, higher priority for protection.
- Documentation: Clearly document each identified asset, its location, its role in the system, and any protection mechanisms currently in place. This documentation is crucial for ongoing risk management and ensuring that all team members have a consistent understanding of the system’s components.
- TARA Execution Steps
- Asset and Threat Identification: With the system’s assets clearly defined, identify the specific threats applicable to each asset, using the earlier threat modeling as a guide.
- Scenario Development: Develop scenarios for each identified threat, focusing on envisioning the potential outcomes of an attack without delving into the technical specifics of how the attack is carried out.
- Impact and Likelihood Estimation: For each threat scenario, estimate the potential impact on stakeholders and the likelihood of the threat occurring. This involves assessing factors like safety, financial loss, operational disruption, and privacy breaches.
- Risk Classification: Utilize methodologies like Heavens or SAHARA to classify the risk associated with each threat. This step combines the estimated impact and likelihood into a comprehensive security level rating.
- Cybersecurity Goal Definition: Based on the identified risks, define specific cybersecurity goals for each significant threat. These goals outline the high-level protections or risk mitigation strategies that need to be implemented.
- Requirement Specification: Finally, translate the defined cybersecurity goals into actionable high-level cybersecurity requirements. These requirements are aimed at addressing the identified risks, thereby enhancing the system’s security posture against potential cyber attacks.
Performing Threat Analysis and Risk Assessment for a Telematics ECU
Cybersecurity risks are more pronounced in connected systems of a vehicle, for eg. Telematics ECU. Vehicle telematics system by the virtue of being connected to the outside world are vulnerable to cyberattacks.
So, let’s understand TARA in finer details by dissecting the cybersecurity vulnerabilities of a Telematics system.
This example serves to illustrate the application of TARA in a simplified and abstracted manner, specifically during the concept phase of system development. It outlines a systematic approach to cybersecurity risk management, focusing on identifying and assessing potential threats and vulnerabilities within the system, and deciding on appropriate risk treatment options.
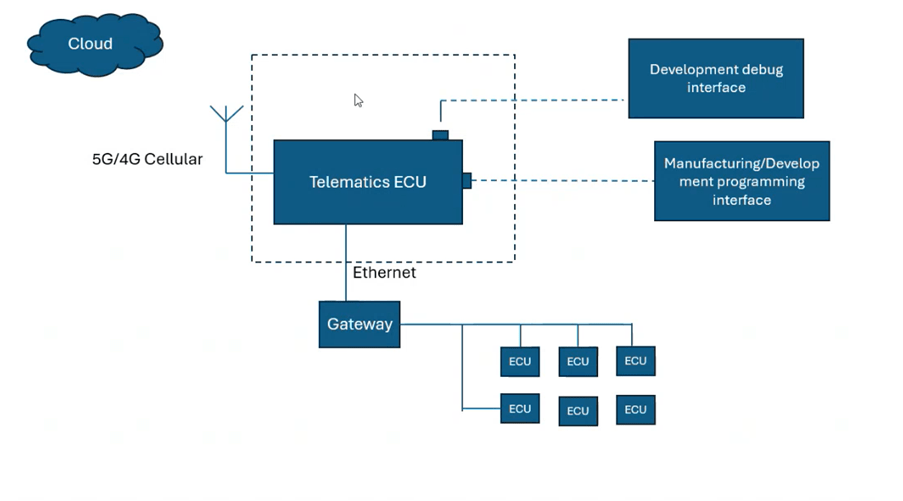
The output of each step in TARA is an input to the next step. For example, based on the damage scenarios identified during ‘asset identification’ step, cybersecurity experts derive the threat scenarios. Subsequently, the ‘threat scenarios’ become the input for the next step, i.e. Risk determination and treatment and so on..
Let’s get back to TARA of a Telematics ECU!
Item Definition for Telematics ECU
Item Boundary & Functions: The TCU, responsible for telematics services like emergency calls (eCall), remote diagnostics, vehicle tracking, and firmware updates over-the-air (FOTA).
Preliminary Architecture: Encompasses integration of cellular modules, GPS, and interfaces for Vehicle-to-Everything (V2X) communications, highlighting the interaction with internal and external networks.
Asset Identification
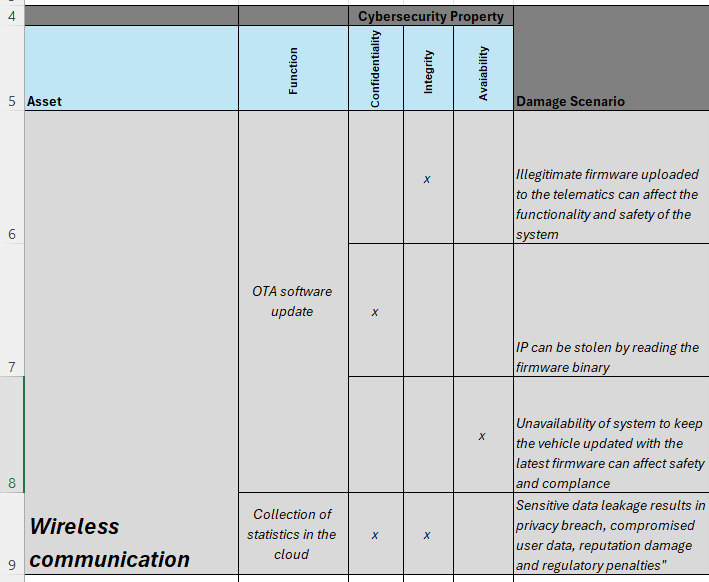
One of the assets of Telematics ECU for cybersecurity consideration is the wireless communications. We mention the functionality of this asset and further dissect the cybersecurity properties pertaining to wireless communications. As per the template prescribed by ISO 21434 standard, confidentiality, integrity, and availability are three properties that we consider for TARA.
Damage Scenarios: Potential damages involve unauthorized access to vehicle tracking information, injection of malicious firmware updates, and breach of user privacy.
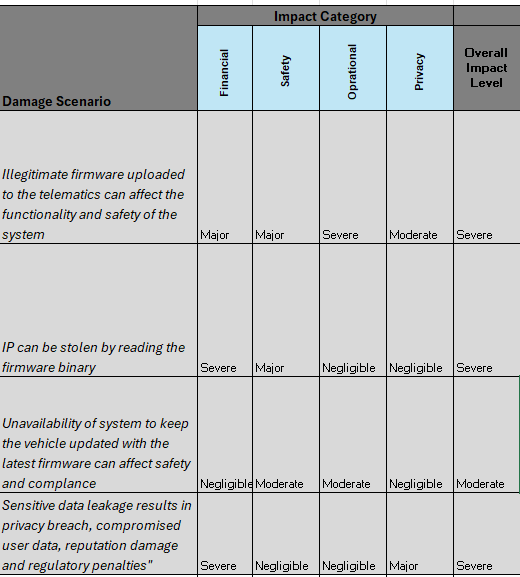
Impact Rating
Applies the scale from “Negligible” to “Severe” to evaluate how threats could impact safety, privacy, and operational functionality. For example, a breach in user privacy through unauthorized access to personal data could be rated as “Major” or “Severe” due to legal and reputational consequences.
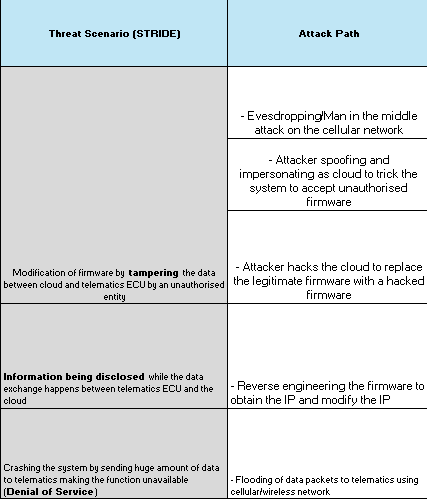
Threat Scenario Identification
Uploading of illegitimate firmware: Such a scenario can affect the functionality and safety of the telematics ECU.
Leakage of sensitive data: It can lead to privacy breaches and its adverse repercussions including regulatory penalties.
Attack Path Analysis
External Communication Compromise: An attacker might exploit vulnerabilities in cellular or Wi-Fi connections to gain access to the TCU, aiming to manipulate telematics functions or steal sensitive data.
Attack Feasibility Rating
Feasibility is assessed based on the attacker’s required resources and expertise. For instance, an attack exploiting a well-known vulnerability in the TCU’s cellular module might be rated as “High” feasibility due to the availability of exploit tools and knowledge.
Risk Value Determination
Combines the impact and feasibility ratings to prioritize threats. High-risk scenarios might include those that could lead to direct safety impacts or significant breaches of user privacy.
Risk Treatment Decision
For a TCU, risk reduction through technical controls, such as enhanced encryption for data transmission and robust authentication mechanisms for firmware updates, is typically preferred to protect against identified threats.
Cybersecurity Strategy for TCU
- Layered Security: Employment of network segmentation and firewalls, and IDS to safeguard the TCU’s network interfaces.
- Secure Communication: Implementation of end-to-end encryption for all transmitted data to prevent interception or manipulation.
- Software Management: Ensuring secure FOTA processes with cryptographic verification to maintain firmware integrity.
- Anomaly Detection and Incident Response: Utilization of advanced monitoring for the TCU’s network activity and establish a clear protocol for responding to detected cybersecurity incidents.
Conclusion
A well-executed TARA process offers comprehensive insights into the potential vulnerabilities within a system, the likely threats that could exploit these vulnerabilities, and the potential impact of such exploits on the system’s operations and stakeholders.
The culmination of the TARA process in the risk treatment decision step is crucial for defining actionable strategies to mitigate identified risks.
By applying a thorough and methodical approach to threat analysis and risk assessment, organizations can enhance their preparedness against cyber-attacks, protect critical assets, and ensure the continuity of their operations.
Embitel Technologies has proven expertise in performing TARA as per ISO 21434 standard. Our automotive cybersecurity team can support you in end-to-end cybersecurity requirements.



