The idea of remote diagnostics of a vehicle sounds very exciting. And so does the convenience of updating a car’s software without visiting the garage. It seems like a win-win for the car users as well as the OEMs and service centers. However, it is important to be aware of the security risks that can wreak havoc once a cyberattack cripples the car electronics system and steals valuable data. Especially, when external TCP/IP protocols are involved, securing the network becomes an uphill task. But should that mean an end to remote diagnostics and Firmware over the air (FOTA) upgrade? Absolutely no!
Cybersecurity comes across as a cornerstone that boosts consumer confidence on advanced technologies such as V2X, V2V, autonomous driving and more.
Thanks to the automotive cybersecurity standards such as ISO 21434, there are clear guidelines and best practices to secure the vehicle network. Among various technologies and security layers, Transport Layer Security (TLS) stands out, especially when protocols such as DoIP are involved. This is because DoIP uses Transport layer to communicate to ECUs and naturally, Transport Layer Security module is the best fit, almost like ‘made for each other’.
We, at Embitel have been delivering solutions around cybersecurity to many of our customers. From secure bootloaders to secured DoIP protocols using TLS, cybersecurity has been at the crux of our innovations.
What is Transport Layer Security?
Transport Layer Security is a shield to secure the Transport Layer of a communication protocol such as DoIP (ISO 13400). TLS protects the data from being stolen or modified when it is being transmitted from a server to client or vice-versa. TLS can be seen as an implementation of cybersecurity protocol. It is essentially a high-level cybersecurity protocol under which there are protocols for specific requirements. The beauty of a TLS module is that it can be easily tailored to the specific requirements of a project.
Looking closely at TLS module, we observe that it comprises of sub-protocols. One of them is the handshake protocol that establishes a type of encrypted understanding between the server and client. During the handshake session, the server and client exchange relevant data to identify and authenticate each other. Session keys and encryption algorithm to be used, will be established. Once the handshake is over, the actual transmission of data takes place.
Similarly, the record protocol ensures the confidentiality and the integrity of the data to be transmitted between the entities. It makes use of symmetric cryptography to achieve that.
At the core of Transport Layer Security module are cipher suites. These are nothing but algorithms that help secure the connection.
The latest version of a transport layer security module comprises the following cipher suites.
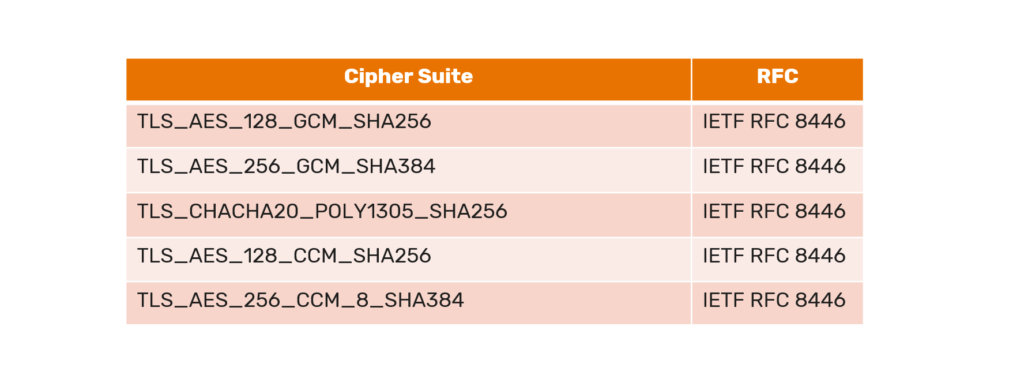
During a secure communication, the client will inform the server about which cipher suite it supports. The server will match the cipher suite supported by client to its own. If it matches, the server notifies the client that a secure communication may be established.
TLS module works as a standalone module which can be appended with any kind of TCP/IP communication irrespective of the upper application layer.
Whether it is remote vehicle diagnostics using DoIP as the transport protocol and UDS as the application layer or a FOTA application, TLS can be readily used to secure the communication.
Implementation of TLS in Remote Vehicle Diagnostics Powered by DoIP
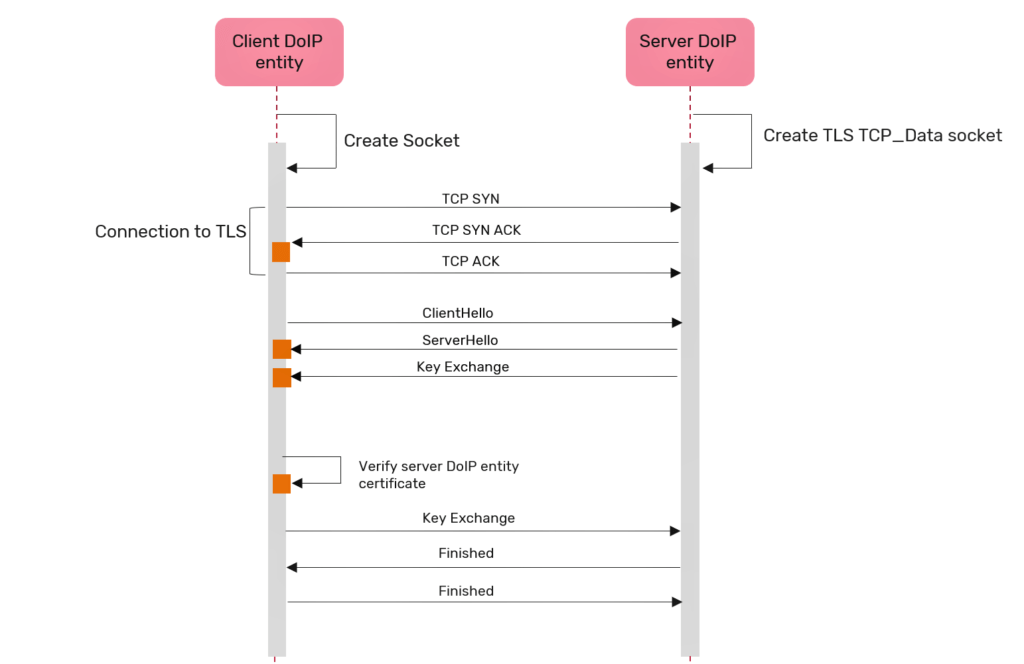
DoIP stands for Diagnostics over Internet Protocol, a de facto standard for remote vehicle diagnostics used across OEMs. Since, it uses TCP for communication, TLS proves to be the perfect fit for securing the connection between the client DoIP entity and server DoIP entity.
TLS helps in establishing a secure connection which is both:
- Authenticated: Entails the authenticity and integrity of the data to be communicated.
- Encrypted: Protection of confidentiality through encrypted communication between client and server.
TLS protocol is implemented by the secure diagnostic communication for the transport channel between DoIP server and client. Prior to exchanging DoIP messages, a secure TCP connection is negotiated using TLS handshake protocol. The server and the client entity exchange versions of TLS protocol, decide the common cipher suite, verify certificates and complete the session key exchange.
Implement Automotive Cybersecurity with Solutions from Embitel
Automotive cybersecurity has been one of Embitel’s focus areas in terms of solution development and innovations. Different teams within the automotive and IoT verticals have been working on various use-cases and implementation of automotive cybersecurity. Transport Layer Security, being a major aspect of cybersecurity, has been at the core of our innovations. Following are some of the implementations of automotive cybersecurity technology that our team has successfully developed and delivered.
TLS Equipped with DoIP Software: Our ready-to-integrate DoIP software now comes equipped with TLS module for enhanced security. We can also integrate TLS module for existing customers who have implemented our DoIP stack in the past. Whether it is the latest TLS 1.3 or older versions we will provide end-to-end TLS module implementation.
TLS Equipped FOTA: We have our IoT team also working parallelly on cybersecurity aspect of telematics and general FOTA applications. We can implement TLS module for such IoT applications as well.
Secure Bootloader: Our foray into automotive cybersecurity actually began with secure bootloader implementation for few of our clients. Similar algorithms with SHA 128/256 encryption have been used for developing secure bootloaders. More on secure bootloader in the next section.
Customer Success Story: Development and Integration of Secure Bootloader
Business Context:
Applications like ADAS, Telematics, Body Control Modules require flash Bootloaders for timely ECU re-programming. Since many of these applications use OTA upgrades, the bootloader must be equipped with security features such as Digital Signature, Encryption, Hardware Security Module, and others. We understood the requirements from our customers and started to work on various algorithms to be used for a secure bootloader.
Our Solution:
We have equipped our Secure Bootloader solution with five security components- AES-128, Digital Signature, CRC32, HMS Drivers, Secondary Bootloader (SBL).
Secure Bootloader Solution Overview:
- We have used AES 128 algorithm for encryption/decryption of the software update patch (image file). Data is secured using the AES 128 algorithm prior to sending it to the vehicle ECU from the flashing device.
- Our secure Bootloader solution utilizes SHA 256 Algorithm for Digital Signature. The target ECU validates this digital signature before downloading the file.
- CRC32 algorithm is used an error detecting code to ensure data integrity. Any corruption in data will be identified by CRC32 and prevent it to be downloaded to the ECU.
- Hardware Security Module integrated within the Bootloader implements hardware level security. It also works with AES algorithm to augment the security of the communication through bootloader.
Automotive cybersecurity using Transport Layer Security module is getting wide-spread acceptability. Connect with us to implement TLS module within your automotive projects related to remote vehicle diagnostics, telematics and FOTA.



